Check Point: 's SSL Inspection Technology | Enterprise Network Security, Check Point: Through the Years HD
00:07:06
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
31285 просмотров на сайте 12n.ru
's SSL Inspection Technology | Enterprise Network Security.
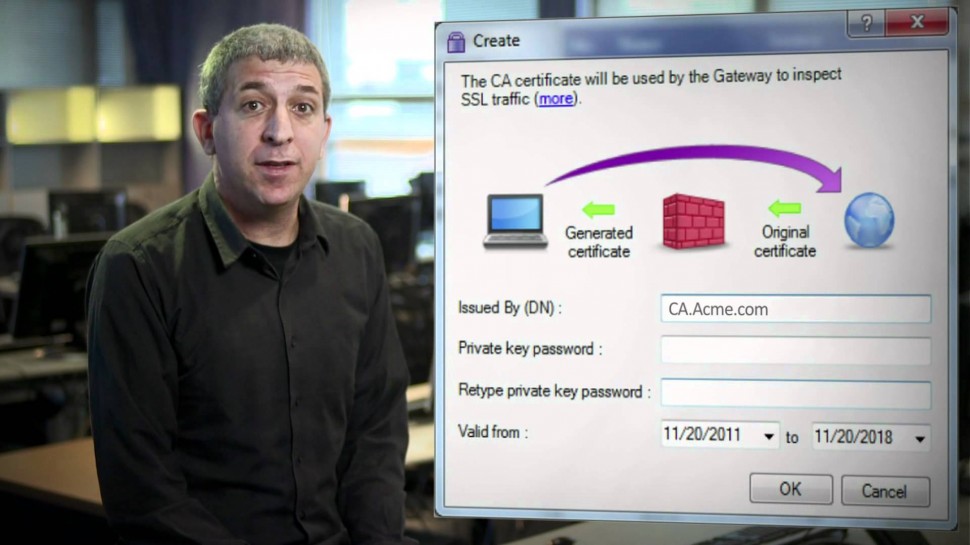
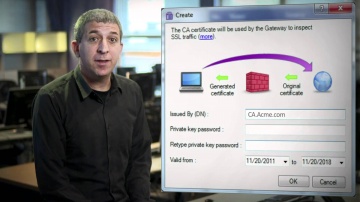
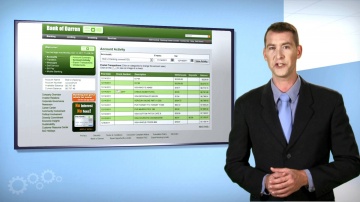
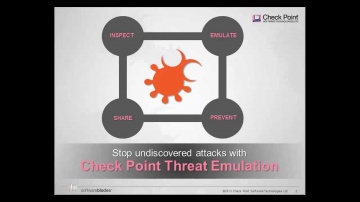
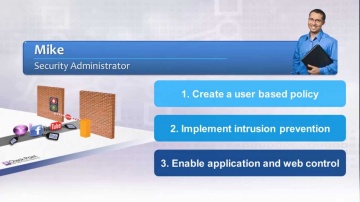
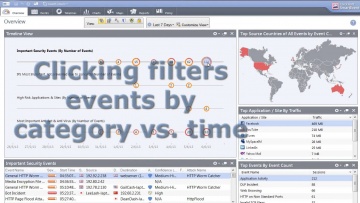
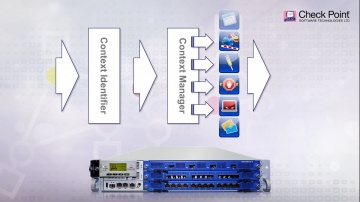
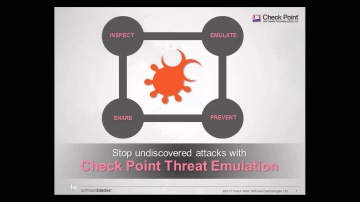
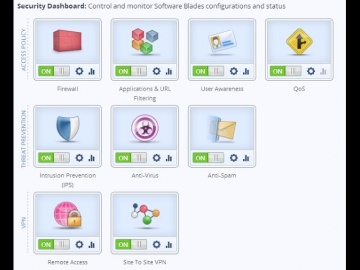
This video shares 's SSL Inspection technology against internal and external threats: This video provides a close look at 's SSL Inspection technology, which allows 's advanced security functions — including Application Control, URL Filtering, IPS, DLP, and more — to analyze the contents of encrypted network traffic, giving your organization even stronger protection from both external and internal threats.Visit our website for more information:
развернуть свернуть














































כמו במקרה של כרום וGoogle.com?