Check Point: Technical Assistance Center | Network Security Support, Check Point: How-to and Tutorials HD

00:02:24
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
1915 просмотров на сайте 12n.ru
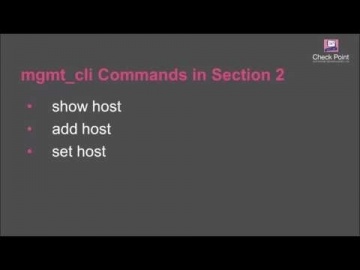
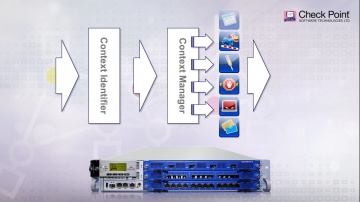
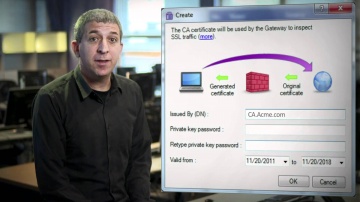
Technical Assistance Center | Network Security Support.
's team of vigilant security experts are here to help our customers. Well trained engineers are available to assist you 24/7 via web service request, live chat, or by phone.For more information:
развернуть свернуть