Check Point: Through the Years плейлист

360 роликов
Нет подписчиков
Компания Check Point Software Technologies Ltd. — мировой поставщик решений в области обеспечения интернет-безопасности, единственный поставщик средств обеспечения полной безопасности Total Security для сетей, данных и конечных узлов, объединенных единой средой управления.
Check Point: Through the Years
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вредоносного ПО и отражения других типов атак.
предлагает законченную архитектуру безопасности, которая защищает и сети крупных организаций, и мобильные устройства, а также отличается наиболее полным и интуитивно понятным управлением системой безопасности. стал первопроходцем в индустрии с межсетевым экраном FireWall-1 и запатентованной технологией Stateful Inspection.
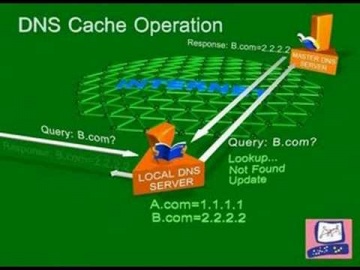
Check Point: DNS Cache Poisoning Attack | Internet Security
Software explains common DNS attacks. Learn More: DNS is the glue that holds the Internet, including web and e-mail together. A successful attack may severely impact the availability of an organization’s public facing web sites and e-mail...
Cмотреть видео
Cмотреть видео
Check Point: WebCheck
For more information visit: WebCheck protects the enterprise against the rising number of web based threats with a simple, transparent user experience. WebCheck isolates against known and unknown web threats with browser virtualization ...
Cмотреть видео
Cмотреть видео
Check Point: opens NASDAQ
Gil Shwed, CEO of Software Technologies, Ltd., opens NASDAQ on 12 August 2009.
Cмотреть видео
Cмотреть видео
Check Point: ZoneAlarm vs. Windows 7
Microsoft has made a much anticipated new operating system. However, the hackers will continue to find ways to bypass whatever security measures the operating system puts in place. Due to the fact consumers should use an advanced security s...
Cмотреть видео
Cмотреть видео
Check Point: Choosing the right endpoint security solution
For more information: Fred Borjesson regional endpoint sales manager at Software Technologies discusses the best ways for enterprises to manage their endpoint security and explains the benefit of using one unique single endpoint security...
Cмотреть видео
Cмотреть видео
Check Point: IPS Software Blade
SSL Certificates attacks can compromise even the most secure sites. Learn how s IPS solutions protect against this specific kind of threats.
Cмотреть видео
Cмотреть видео
Check Point: Makes DLP Work | Data Loss Prevention
's new DLP Software Blade combines innovative technology with a unique approach that blocks intentional and unintentional data breaches and educates employees in the process to help prevent future incidents. Watch this video to see how...
Cмотреть видео
Cмотреть видео
Check Point: 3D Security.mov
For more information visit: 3D Security vision redefines security as a 3-dimensional business process that combines policies, people and enforcement for stronger protection across all layers of security—including network, data and endpoi...
Cмотреть видео
Cмотреть видео
Check Point: Software Opens NASDAQ on 15th Year Anniversary of IPO
Founder, chairman and CEO, Gil Shwed, along with Tal Payne, the chief financial officer, and the company's board of directors participated in The NASDAQ Opening Bell ceremony at The NASDAQ Stock Market on Tuesday, June 28, 2011. The ceremon...
Cмотреть видео
Cмотреть видео
Check Point: Data Centers Security Struggle
Gil Shwed, CEO of Software, talks with James Rogers of TheStreet.com
Cмотреть видео
Cмотреть видео
Check Point: 3D Security
TheStreet.com Gil Shwed, CEO of Software, talks with James Rogers of
Cмотреть видео
Cмотреть видео
Check Point: Cyber Security Plays Offense | Cyber Security
For more information: Gil Shwed, CEO of talks to James Rogers of TheStreet.com
Cмотреть видео
Cмотреть видео
Check Point: The Threat of Bots and Botnets | IoT | Network Security
Learn More: explains: What is a bot? What is a botnet? What is an Advance Persistent Threat?
Cмотреть видео
Cмотреть видео
Check Point: Advanced Network Security: New Anti-Bot Software Blade
Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention. More information: provides organizations of all sizes with the latest data and network security protection i...
Cмотреть видео
Cмотреть видео
Check Point: Unveils New Network Security Appliance Models
Gabi Reish, Head of Product Management at Software Technologies, introduces the new 2012 line of Appliances. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated...
Cмотреть видео
Cмотреть видео
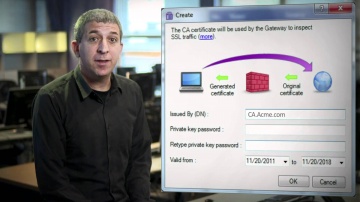
Check Point: 's SSL Inspection Technology | Enterprise Network Security
This video shares 's SSL Inspection technology against internal and external threats: This video provides a close look at 's SSL Inspection technology, which allows 's advanced security functions -- including Application Control, URL Fil...
Cмотреть видео
Cмотреть видео
Check Point: Protecting Against Spy Eye Bot | Network Security
For more information: Learn how to protect against Spy Eye bot
Cмотреть видео
Cмотреть видео
Check Point: Anti-Bot Protection | IoT| Network Security
A bot is malicious software that allows cyber criminals to remotely control computers and execute illegal activities such as stealing data, spreading spam and distributing malware. More information: Anti-Bot security software detects bot...
Cмотреть видео
Cмотреть видео
Check Point: Overview of the 61000 Appliance | Data Center Security Systems
For more information:
Cмотреть видео
Cмотреть видео
Check Point: Denial of Service Attacks & How to Protect Against Them
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Alon Kantor, Corporate Development Architect at talks about the threat of dist...
Cмотреть видео
Cмотреть видео
Check Point: Why Trust Matters for Security
Following a press round table event held in London in December 2012, panelists looked at why trust is fundamental to security, and how organizations can prove that they and their employees can be trusted. The spokespeople are: - Kevin B...
Cмотреть видео
Cмотреть видео
Check Point: Radio Interview Discussing 2013 Cyber Security Threats
Kellman Meghu, Head of Security Engineering at speaks to The Biggs Radio Show about what cyber security threats we should look out for in 2013
Cмотреть видео
Cмотреть видео
Check Point: Next-Generation Secure Web Gateway | Network Security
Learn More: Are you trying to secure Web 2.0 with 1.0 tools? The Web has evolved, threats have evolved, so should your Web Security! In this video, learn how to best protect against today's web-borne malware and help businesses to get th...
Cмотреть видео
Cмотреть видео
Check Point: on National Czech Republic Television
Eurograbber was launched against banking customers, using a sophisticated combination of malware directed at computers and mobile devices. For more information click here: The malware, in conjunction with the attackers' command and contr...
Cмотреть видео
Cмотреть видео
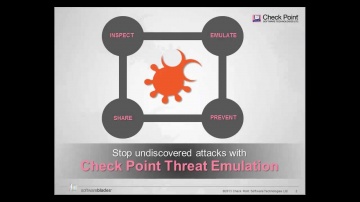
Check Point: DDoS Protector - Technical Overview | DDoS Protection
's new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: This innovative solution quickly inspects suspicious files, emulates how they run to discover mali...
Cмотреть видео
Cмотреть видео
Check Point: 2013 Security Report | Cyber Security
Based on research of nearly 900 companies and 120,000 hours of monitored traffic, the 2013 Security Report reveals major security risks organizations are exposed to on a daily basis. For information: Most importantly, the report provides...
Cмотреть видео
Cмотреть видео
Check Point: Third Party Security Validation | Threat Prevention
For more information: is excited to have received top awards from respected industry sources and certification bodies for its Next Generation Firewall, IPS and Threat Prevention Appliance products.
Cмотреть видео
Cмотреть видео
Check Point: Denial of Service Cyber Attack Protector Overview
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Modern DDoS attacks use new techniques to exploit areas where traditional secu...
Cмотреть видео
Cмотреть видео
Показать больше