Поиск по тегу «data breach» в разделе Видеокаталог
HD 01:01:35
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
HD 00:30:26
Check Point: Who's Responsible for your Cloud Security?
A full breakdown of what is shared responsibility and the layers of security needed to protect you from security breaches in the cloud. For more information:
Cмотреть видео
Cмотреть видео
HD 00:29:43
Check Point: The Mobile Threat Landscape
From Judy to Blueborne, the proliferation of mobile threats has grown rapidly in the past year. In this session, we review the various types of mobile threats, how they spread and the damage they cause. We will also be providing practical ...
Cмотреть видео
Cмотреть видео
HD 00:28:57
Check Point: Best of CheckMates: My Top CLI Commands
This presentation will highlight the most useful CLI commands submitted via CheckMates by real users just like you!+ For more information: Use cases, examples and case studies will be presented for the top CLI commands from the CheckMate...
Cмотреть видео
Cмотреть видео
HD 00:22:22
Check Point: Building a Secure Platform as CIO - CPX 360 Keynote
In his keynote, Sharon Schusheim will discuss what it takes to build and operate a secure platform as a CIO. For more information: CPX 360 promises to be the premier cyber security summit. For the first time, we will bring our customers...
Cмотреть видео
Cмотреть видео
HD 00:01:34
Check Point: Zero-day Threat Protection for SaaS Email | CloudGuard SaaS Demo
Demo showing how CloudGuard Saas provides advanced security and threat prevention for SaaS applications. For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (Saa...
Cмотреть видео
Cмотреть видео
HD 00:05:12
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
HD 00:19:45
Check Point: How to Hack a Cell Phone | Demo for Understanding Mobile Security
Want to hack a Smartphone? A hands-on approach to understanding mobile security. Learn more here: Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is! Learn more:
Cмотреть видео
Cмотреть видео
HD 00:05:18
Check Point: Deployment Tools - ISOmorphic & Blink
Deploying Next Generation Firewalls just got easier with the introduction of the Blink utility. For more information: Blink creates a working snapshot of a cleanly installed security gateway with a completed First-Time Configuration Wizard...
Cмотреть видео
Cмотреть видео
HD 00:01:15
Check Point: Advanced Cyber Attack Business Protection
SandBlast mobile offers the best advanced cyber attack protection for your business. More information: Cybercriminals are better than ever at stealing sensitive information from your smartphone or tablet. Whether it's personal information...
Cмотреть видео
Cмотреть видео
HD 00:04:00
Check Point: SandBlast Mobile: Quick Start Guide | Tech Bytes
This video is meant to show how easily you can get started protecting your Enterprise's Android and iOS Devices with SandBlast Mobile. More information: Topics covered: Ch1 - Activating Your Admin Account Ch2 - Logging into Your SandBlast...
Cмотреть видео
Cмотреть видео
HD 00:24:49
Check Point: Welcome to the Future of Cyber Security | Infinity
The future of cyber security is here. Learn and stay protected against today's cyber threat landscape. For more information: We are all living in a connected world which is affecting every aspect of our lives. In the past couple of ye...
Cмотреть видео
Cмотреть видео
HD 00:17:56
Check Point: Hacking the Smartphone | Mobile Cyber Hack Demonstration
Live demonstration of a smartphone hack, from Experience 2017. For more information visit: Watch Michael Shaulov, Head of Mobility Products at Software hack a smart phone in real time. Today every business is a mobile business, with req...
Cмотреть видео
Cмотреть видео
HD 00:54:57
Check Point: Understanding SandBlast - Zero-Day Protection
Understanding your exposure to threats—and what you can do about it is not only responsible business management—it’s critical to business survival. More information: Turn Security into an Enabler, Not a Disabler. SandBlast Zero-Day Prote...
Cмотреть видео
Cмотреть видео
HD 00:01:56
Check Point: SandBlast Zero-Day Protection | Advanced Threat Prevention
Hackers constantly modify their strategies and techniques to evade detection by traditional sandboxes to reach corporate resources. For more information visit: SandBlast Zero-Day Protection, with evasion-resistant malware detection, pro...
Cмотреть видео
Cмотреть видео
01:03:03
Check Point: Stay One Step Ahead with SandBlast Zero-Day Protection
Watch this webcast to learn about SandBlast Zero-Day Protection, an innovative approach to stop unknown malware, zero-day and targeted attacks from infiltrating networks. More information: Zero-day protection offering network security wi...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:07:07
Check Point: Compliance Software Blade Demonstration
Introduction and overview to the Compliance Software Blade and its features and functions.For more information: The Compliance Software Blade monitors your management, Software Blades and security gateways to constantly validate that you...
Cмотреть видео
Cмотреть видео
HD 00:07:06
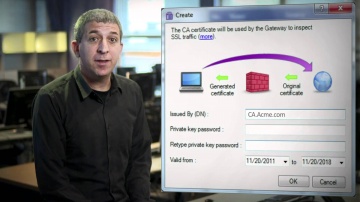
Check Point: 's SSL Inspection Technology | Enterprise Network Security
This video shares 's SSL Inspection technology against internal and external threats: This video provides a close look at 's SSL Inspection technology, which allows 's advanced security functions -- including Application Control, URL Fil...
Cмотреть видео
Cмотреть видео
00:01:45
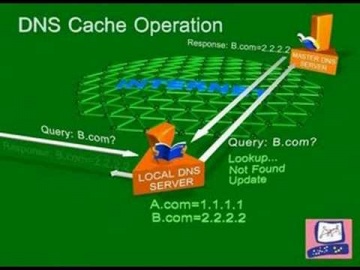
Check Point: DNS Cache Poisoning Attack | Internet Security
Software explains common DNS attacks. Learn More: DNS is the glue that holds the Internet, including web and e-mail together. A successful attack may severely impact the availability of an organization’s public facing web sites and e-mail...
Cмотреть видео
Cмотреть видео