Check Point: Anatomy of a Smishing Attack: Czech Posta App, Check Point: Mobile Security HD
00:02:12
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
1098 просмотров на сайте 12n.ru
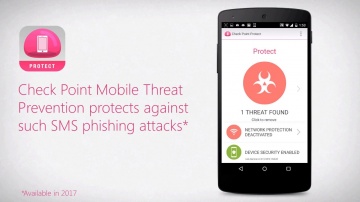
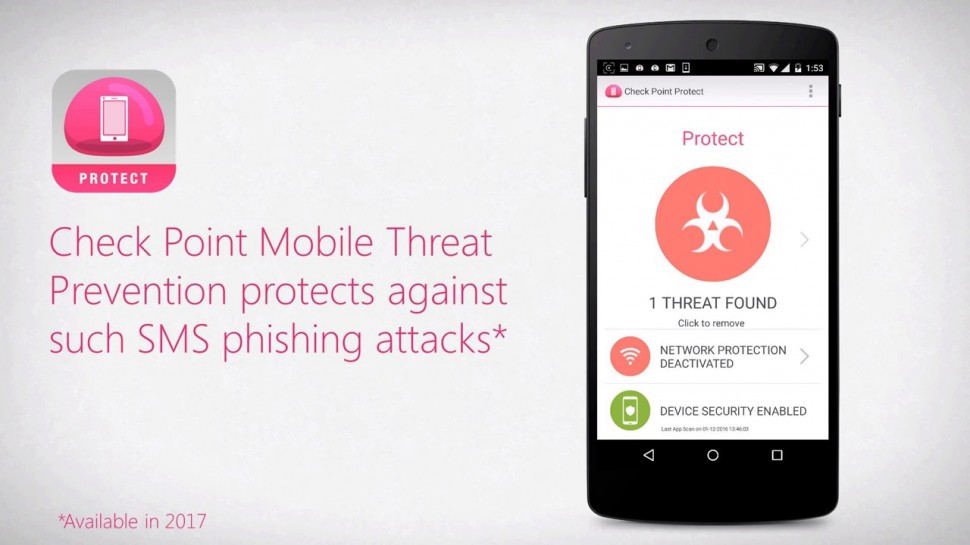
Anatomy of a Smishing Attack: Czech Posta App.
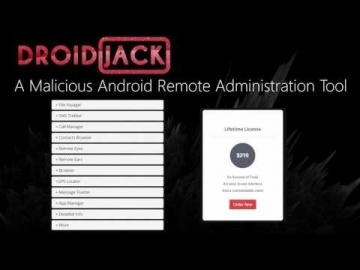
A new smishing attack targeted users in the Czech Republic was discovered January 26, 2017. Smishing, or SMS phishing, is a vector attackers use to send SMS messages from supposedly legitimate organizations. These messages persuade users to download a malicious app, to provide private information like bank account or credit card details, or to click on a malicious URL. In this campaign, the attackers masqueraded as Czech Post, the Czech postal service, to get users to download a malicious app containing a full-scale Trojan horse. Once users click the link, they are led to a fake Czech Post web page with a seemingly legitimate address. From there the malware downloads and installs immediately on the mobile device. Since users need to approve the installation of apps from sources other than Google Play, the attackers use social engineering tactics convincing them to do so.For more information:
развернуть свернуть