Поиск по тегу «phishing» в разделе Видеокаталог
HD 00:05:12
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
HD 00:26:30
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Technical Assistance Center | Network Security Support
's team of vigilant security experts are here to help our customers. Well trained engineers are available to assist you 24/7 via web service request, live chat, or by phone. For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:12
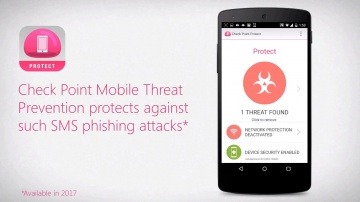
Check Point: Anatomy of a Smishing Attack: Czech Posta App
A new smishing attack targeted users in the Czech Republic was discovered January 26, 2017. Smishing, or SMS phishing, is a vector attackers use to send SMS messages from supposedly legitimate organizations. These messages persuade users t...
Cмотреть видео
Cмотреть видео
HD 00:00:49
Check Point: RSA 2016: Receives "Recommended" Rating in NSS Next Generation Firewall Test
More Information: NSS Labs, Inc. released their results for the 2016 Generation Firewall Test. In their independent assessment of the security effectiveness and value, NSS once again recognized with the "Recommended" rating. This marks t...
Cмотреть видео
Cмотреть видео
HD 00:03:56
Check Point: Customer Success Video: Hotel Nikko San Francisco
Hotel Nikko relies on its network to support guest services, reservation systems, property management and other critical business operations. Keeping the network safe and secure is key, and even a brief outage means lost revenue, disappoin...
Cмотреть видео
Cмотреть видео
00:27:51
Check Point: The Security Zone Ep. 1: Unknown 300 | Enterprise Cyber Security
In recent benchmark testing, 300 malicious files were scanned through Threat Emulation and other competitive products. The results found that outperformed all of the others.
Cмотреть видео
Cмотреть видео
00:03:42
Check Point: Customer Success: The University of Liege Uses To Boost Network Security
The University of Liege in Belgium selects to help mitigate security issues around areas like BYOD and the increasing need for bandwidth. With 's 12600s and 12200s appliances in the data center and 2200s for its branch locations, the Univ...
Cмотреть видео
Cмотреть видео
HD 00:02:58
Check Point: Customer Success Video: MLB Network Maintains 100 Percent Network Uptime
The MLB Network turns to to help launch the cable network and achieve 100 percent uptime. 's easy, flexible and scalable security solution enables the MLB Network to maintain zero downtime and address the needs of its viewing fans in 70 m...
Cмотреть видео
Cмотреть видео
HD 00:02:00
Check Point: Anti-Bot Protection | IoT| Network Security
A bot is malicious software that allows cyber criminals to remotely control computers and execute illegal activities such as stealing data, spreading spam and distributing malware. More information: Anti-Bot security software detects bot...
Cмотреть видео
Cмотреть видео
HD 00:03:31
Check Point: Protecting Against Spy Eye Bot | Network Security
For more information: Learn how to protect against Spy Eye bot
Cмотреть видео
Cмотреть видео
HD 00:03:43
Check Point: The Threat of Bots and Botnets | IoT | Network Security
Learn More: explains: What is a bot? What is a botnet? What is an Advance Persistent Threat?
Cмотреть видео
Cмотреть видео
HD 00:03:18
Check Point: Advanced Network Security: New Anti-Bot Software Blade
Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention. More information: provides organizations of all sizes with the latest data and network security protection i...
Cмотреть видео
Cмотреть видео