Check Point: Advanced Cyber Security for 2018 | Prevent 5th Generation Cyber Attacks with Infinity, Check Point: Threat Prevention HD

00:01:54
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
4318 просмотров на сайте 12n.ru
Advanced Cyber Security for 2018 | Prevent 5th Generation Cyber Attacks with Infinity.
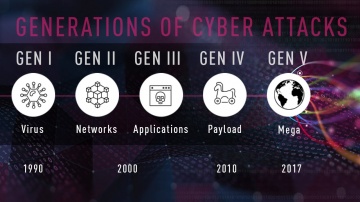
More information: Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the future.TRANSCRIPT:Today’s IT environments have evolved significantly.We’re far more connected than ever as we’re using more devices, more networks, more clouds. However, as our connectivity has evolved so have the cyberattacks. Threats on our IT environments have become more sophisticated and harder to prevent.Today, we are yet again in an inflection point in Cyber security – we are in the 5th generation of threats. Large-scale multi-vectored mega attacks that inflict vast amounts of damage on businesses and their reputation. The paradox is that while the risk has grown exponentially, most enterprises are still using multiple security solutions for the previous generations of threats. Systems that are no longer effectiveThese enterprises are at risk at all levels:They’re exposed to ransomware attacks on their servers in their Data center, and they’re at risk from lateral movements in the cloud that could lead to the loss of confidential information.And of course, they’re exposed to threats on mobile devices, the weak link in today's evolving networks, where malicious applications can steal business data, account numbers, passwords and more.Businesses are not sharing intelligence in real-time and therefore, even if they detect and mitigate an attack from one location, it is still quite probable that the same attack will penetrate their network through another path.And what about managing security with so many different security consoles? It’s time for a change.We must keep up and the businesses’ security level cannot stay behind. We must use the fifth generation of security protections with a security architecture that sees the entire enterprise as a whole. A solution that is able to prevent these mega-attacks in real-time before they even happen.A solution that is up to date with the best security technologies, and is able to share threat intelligence across the entire IT infrastructure.That’s where Infinity comes in.
развернуть свернуть