Check Point: Welcome to the Future of Cyber Security | Infinity, Check Point: CyberTalks - Experience 2017 HD

00:24:49
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
5060 просмотров на сайте 12n.ru
Welcome to the Future of Cyber Security | Infinity.
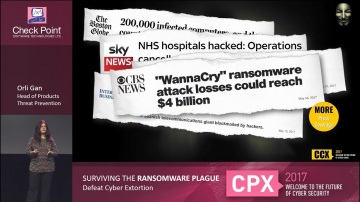
The future of cyber security is here. Learn and stay protected against today's cyber threat landscape. For more information: We are all living in a connected world which is affecting every aspect of our lives. In the past couple of years, we have been discussing implications of a technology and digital-driven world (i.e.) cloud, mobile, advanced threats. Today, we are seeing some of our worst predictions shaping into real life. So why are businesses not protecting themselves and instead keep making excuses? In today’s world, business need security that meet their business needs. Gil Shwed's discussion defines the pillars of security that businesses should adopt, based on their actual business needs.Gil Shwed — Founder and CEO, Software
развернуть свернуть