Поиск по тегу «threat emulation» в разделе Видеокаталог
HD 00:04:12
Check Point: SandBlast Agent Protects From Advanced Zero-day Malware
What happens if employees roam outside enterprise network that protect them from advanced zero-day invasions? For more information: SandBlast Agent protects the enterprise end-points from advanced zero-day malware, by using advanced C-P-U...
Cмотреть видео
Cмотреть видео
HD 00:03:41
Check Point: Overview of SandBlast Agent Forensics Report | Tech Bytes
This video provides an overview of SandBlast Agent’s Forensics Report. SandBlast Agent defends endpoints and web browsers with a complete set of real-time advanced browser and endpoint protection technologies, including Threat Emulation, T...
Cмотреть видео
Cмотреть видео
HD 00:03:15
Check Point: Installing SandBlast Agent on the Enterprise Endpoint
This video provides an overview of recommended process for deployment of SandBlast Agent on the Enterprise Endpoints. SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, including T...
Cмотреть видео
Cмотреть видео
HD 00:02:35
Check Point: SandBlast Agent Backs Up Anti-Virus by Preventing Recently Discovered Malware | Tech By
What happens if your anti-virus signature database is not updated with a very recently discovered malware? SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, by using the up-to-date...
Cмотреть видео
Cмотреть видео
HD 00:07:14
Check Point: Creating Host Objects with R80 Management API Tutorial | Security Management Tutorial
How to use R80 Management API to run a BASH script that automatically creates host objects in the Security Management server database. For more information: This video tutorial is intended for users that are familiar with automation scri...
Cмотреть видео
Cмотреть видео
HD 00:12:19
Check Point: Entrevista a Francisco Robayo, sobre los delitos en la red Teleamazonas Ecuador
Francisco Robayo, Gerente IngenierÌ_a,
Cмотреть видео
Cмотреть видео
HD 00:02:42
Check Point: SandBlast Cloud Advanced Threat Prevention for Microsoft Office 365 | Email Security
Dramatic growth in the use of cloud-based email for the enterprise brings with it an array of security risks, including susceptibility to sophisticated cyber attacks such as ransomware and APTs which use email as a primary entry point. San...
Cмотреть видео
Cмотреть видео
HD 00:02:47
Check Point: ã»âÎÙÄ_Ä_â±Ä â£Ä_â¡ÄÈÄÁÄÄâÈÄ_âü¬»à_¤¼ÄÔ_¨¥ã¬ø
2016_«3¾ÏöÛÄÔÄ_â¢ÄÇÄöÄÄÄÄöÄøÄ_âøâ_øCEOÇâöâÜÄÑÄ_Ä¢Ä_âáĤÄ_Ü¥ÓÈâÕÉÂÐÜÑ_ÑÙÛâÒÁâä¨Ü¥ÓȤøÛÄÔÄ_â¢ÄÇÄö__¨üÈ_µÇø_Ñ_ÇЪ_Ûã_ܨÄâ_Ä_ÄöÇ_ã_...
Cмотреть видео
Cмотреть видео
HD 00:01:42
Check Point: 時代はゼロデイからゼロセカンド(秒)へ – サンドボックス機能比較
時代はゼロデイからゼロセカンド(秒)へ。セキュリティの脅威への対応が1分遅れただけでも取り返しのつかないことになる今日、いかに早く脅威を阻止するかが重要です。
Cмотреть видео
Cмотреть видео
HD 00:01:56
Check Point: サンドボックス機能のカギはCPUレベルの検査とOSレベルのサンドボックス分析
チェック・ポイントのサンドボックスはCPUレベルの検査とOSレベルのサンドボックス分析を組み合わせて、危険性の高い攻撃コードやゼロデイ攻撃、標的型攻撃による感染を防ぎます。
Cмотреть видео
Cмотреть видео
HD 00:02:29
Check Point: Customer Success: Community Newspaper Group (CNG)
For More Information: Community Newspaper Groups seventeen newspapers provide readers with the latest in local news, sports, and entertainment in Perth, Australia. As a publishing outlet, its critical for Community Newspaper Group to kee...
Cмотреть видео
Cмотреть видео
HD 00:00:43
Check Point: Customer Quote: ThreatCloud Emulation Discovers and Prevents Zero-Day Attacks
Gimv IT Manager Kristof Poppe comments on 's Threat Emulation and zero day attacks.
Cмотреть видео
Cмотреть видео
HD 00:00:27
Check Point: Customer Quote: ThreatCloud Emulation Integrated into Software Blade Architecture
Gimv IT Manager Kristof Poppe comments on 's ThreatCloud Emulation integrated into the Software Blade Architecture for layered security.
Cмотреть видео
Cмотреть видео
HD 00:02:50
Check Point: Threat Emulation Protects Investment Firm: Gimv
Learn More: Gimv, a leading European private equity and venture capital investment company, leverages ThreatCloud Emulation technology to prevent against zero day attacks. Watch as IT Manager Kristof Poppe discusses his experience wi...
Cмотреть видео
Cмотреть видео
HD 00:01:43
Check Point: Malware Threat Prevention | Zero-Day, Zero-Second.
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As ...
Cмотреть видео
Cмотреть видео
HD 00:01:58
Check Point: Threat Prevention: Receives Top Marks For Zero-Day Malware Block Rates
In a world of ever-changing cyber threats, organizations are facing the unprecedented growth of unknown malware. These attacks focus on stealing data, sabotaging business continuity, or damaging a company’s reputation. To protect against th...
Cмотреть видео
Cмотреть видео
HD 00:03:59
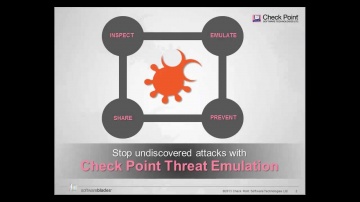
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:04:23
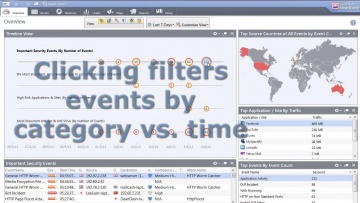
Check Point: SmartEvent | Security Management Walk-Through
Are you tired of managing security by manually searching through millions of logs to find the information you need? There is a better way! Watch this SmartEvent Video to learn how to manage your security more efficiently. For more informa...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: DDoS Protector - Technical Overview | DDoS Protection
's new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: This innovative solution quickly inspects suspicious files, emulates how they run to discover mali...
Cмотреть видео
Cмотреть видео