Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
GroupIB: Как выбрать правильный сайт для покупки авиабилетов
Каждый день в интернете появляются мошеннические сайты, который продают фальшивые билеты. На что стоит обратить внимание, выбирая сайт для покупки авиабилетов? Первое - загляните на ресурс настоящийбилет.рф, который запустили трэвел-компан...
Cмотреть видео
Cмотреть видео
Layta: Falcon Eye FE-AC200G - Фотоловушка
Обзор фотоловушки Falcon Eye FE-AC200G Ссылка:
Cмотреть видео
Cмотреть видео
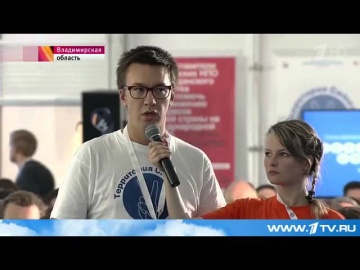
GroupIB: Президент России Владимир Путин ознакомился с решением Bot-Trek Cyber Intelligence
Президент РФ Владимир Путин во время посещения форума "Территория смыслов 2015" познакомился с ведущими разработками специалистов в области IT-технологий. На стенде Group-IB и ФРИИ главе государства продемонстрировали уникальную разработку...
Cмотреть видео
Cмотреть видео
Код Безопасности: Обеспечение защиты виртуальных инфраструктур с vGate
Демонстрация возможностей сертифицированного средства защиты виртуальных инфраструктур с vGate.
Cмотреть видео
Cмотреть видео
Layta: PERCo-TTR-08A - Турникет электромеханический уличный
Турникет-трипод TTR-08А из нержавеющей стали – современное решение для организации контроля доступа с возможностью эксплуатации на открытом воздухе. Основным преимуществом турникета PERCo-TTR-08А является наличие автоматических планок «Ант...
Cмотреть видео
Cмотреть видео
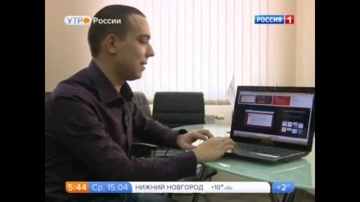
Информзащита: Эксперт «Информзащиты» в передаче «Утро России» на телеканале «Россия 1»
Сегодня страницы социальных сетей накапливают огромное количество информации о каждом пользователе, и это не всегда безопасно. Возникает вопрос, можно ли полностью стереть из сети свои личные данные? Специалист по защите данных компании «Ин...
Cмотреть видео
Cмотреть видео
Layta: Детектор скоплений людей Macroscop
Автоматический выбор лиц из видеопотока. Вы выбираете камеры и время, за которое необходимо просмотреть все лица, попавшие в поле зрения камер, и получаете базу лиц. Выбрав заинтересовавшее лицо, вы можете просмотреть все отрезки архива, гд...
Cмотреть видео
Cмотреть видео
Layta: Зачем нужен досмотровый металлодетектор
Наглядная демонстрация, сколько оружия может быть спрятано у одного человека, и почему необходимо применение досмотровых металлодетекторов.
Cмотреть видео
Cмотреть видео
Check Point: Preventing Tomorrow's Cyber Security Threats
Increasing your enterprise security often means increasing your complexity and management challenges in kind. For more information, visit Growing complexity in security infrastructure puts a huge strain on the efficiency of the security o...
Cмотреть видео
Cмотреть видео
Layta: Контроль активности персонала
Контроль активности персонала Macroscop – в режиме Real Time поможет осуществить мониторинг активности персонала в контрольных зонах. Дополнительно возможно построение отчетов в графическом виде по каждой из шести зон за необходимый временн...
Cмотреть видео
Cмотреть видео
GroupIB: Нигерийские письма счастья
ТВ Центр. Программа "Полезная экономика" Нигерийские письма - это один из видов очень распространённого мошенничества в сети Интернет. Эксперт компании Group-IB Сергей Никитин дал несколько полезных советов, как рассмотреть уловку и не поп...
Cмотреть видео
Cмотреть видео
GroupIB: Хакер взял под контроль самолет, сидя в пассажирском кресле
НТВ. Программа "Анатомия дня" Настоящую панику в США вызвало признание одного из местных хакеров. Крис Робертс сообщил, что, находясь в кресле пассажира, взломал систему управления самолетом. Причем не просто взломал, а якобы вмешался в ра...
Cмотреть видео
Cмотреть видео
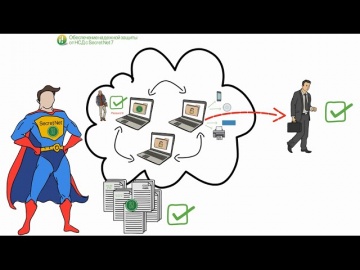
Код Безопасности: Контроль файлов и приложений в Secret Net 7
Демонстрация настройки механизмов контроля целостности и замкнутой программной среды в Secret Net 7.
Cмотреть видео
Cмотреть видео
Check Point: Stopping The Next Cyber Attack | Threat Prevention
Understanding your exposure to threats—and what you can do about it is not only responsible business management—it’s critical to business survival. Turn Security into an Enabler, Not a Disabler. offers network infrastructure security, ant...
Cмотреть видео
Cмотреть видео
Layta: «Прямая линия» с президентом. Комментарии от Михаила Левчука
Михаил Левчук принял участие в прямой линии с президентом В. Путиным и обсудил, что конференция обещает рынку систем видеонаблюдения. Михаил Левчук заместителем гендиректора предприятия «Аргус-Спектр»
Cмотреть видео
Cмотреть видео
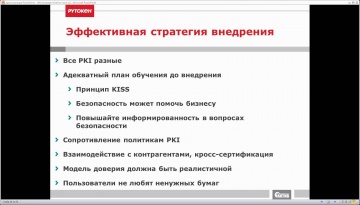
Актив: Вебинар «Roadmap внедрения PKI в корпоративных сетях»
Вебинар посвящен внедрению инфраструктуры открытых ключей и двухфакторной аутентификации в корпоративных сетях. Подробная информация:
Cмотреть видео
Cмотреть видео
GroupIB: Современные способы отъёма денег у населения в Интернете
По оценке экспертов только за год киберпреступники украли 2,5 млрд. долларов. Какие существуют способы обмана в интернете, рассказывает Сергей Никитин, эксперт Group-IB
Cмотреть видео
Cмотреть видео
Актив: Вебинар «iDecide и Рутокен. Новые возможности для управления»
Совместное использование продуктов iDecide и Рутокен BlueTooth. Обеспечение безопасности решений управления бизнесом iDecide при работе на мобильных устройствах.
Cмотреть видео
Cмотреть видео
Layta: Миниатюрная IP камера ACUMEN AiP-C24W-05Y2W в действии
Миниатюрная IP камера AiP-C24W-05Y2W "Коув" предназначена для установки внутри банкоматов и позволяет транслировать в сеть до 4-х потоков одновременно с максимальным разрешением 2Mpx (1920x1080). Сетевая IP видеокамера состоит из видеомодул...
Cмотреть видео
Cмотреть видео
Layta: Beward DS03M/DS03MP - IP видеопанель вызывная
Обзор IP видеопанелей вызывных Beward DS03M и DS03MP
Cмотреть видео
Cмотреть видео
Layta: Индивидуальный дизайн камер видеонаблюдения My Activecam
Компания DSSL предлагает изготовить камеры видеонаблюдения по индивидуальному эскизу заказчика, кроме того специальное приложение позволит выбрать из готовых решений прибор с оригинальным дизайнерским исполнением.
Cмотреть видео
Cмотреть видео
Layta: Революционное решение по защите системы видеонаблюдения от вандализма
Авторы видео - компания DSSL
Cмотреть видео
Cмотреть видео
GroupIB: Топ-5 способов кражи денег с банковских карт
Повсеместное использование пластиковых карточек привлекает многих мошенников, они постоянно находят все новые способы, чтобы добывать информацию о пластиковых картах и снимать с них деньги. Специалисты Group-IB – специализирующейся на ...
Cмотреть видео
Cмотреть видео
Layta: Мобильный комплекс охраны быстро разворачиваемый
Мобильный комплекс охраны БРК-П от компании Юмирс. Комплекс представляет собой быстро разворачиваемую систему охранной сигнализации предназначенную для создания временных рубежей охраны различной конфигурации протяженностью до 2000 м.
Cмотреть видео
Cмотреть видео
Layta: Аргус-Спектр: Денис Сухов об особенностях системы 'Стрелец Мониторинг'
Система безопасности производства компании «Аргус-Спектр» успешно установлена во всех образовательных комплексах республики Марий Эл
Cмотреть видео
Cмотреть видео
Check Point: Customer Success Video: Hotel Nikko San Francisco
Hotel Nikko relies on its network to support guest services, reservation systems, property management and other critical business operations. Keeping the network safe and secure is key, and even a brief outage means lost revenue, disappoin...
Cмотреть видео
Cмотреть видео
Код Безопасности: Обеспечение защиты от НСД с Secret Net 7
Демонстрация возможностей средства защиты информации от несанкционированного доступа Secret Net 7
Cмотреть видео
Cмотреть видео
Код Безопасности: СЗИ от НСД Secret Net
Как обеспечить надежную защиту от насанкционированного доступа к рабочим станциям и серверам Вашей организации? Secret Net - решение №1 на российском рынке СЗИ от НСД.
Cмотреть видео
Cмотреть видео
Актив: Рутокен Web. Курс молодого бойца. ч.2 от 03.03.2015
Практическое занятие по интеграции продукта Рутокен Web в различные решения
Cмотреть видео
Cмотреть видео
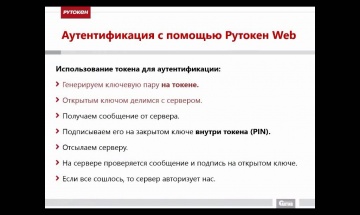
Актив: Рутокен Web. Курс молодого бойца. ч.1 от 03.03.2015
Теоретические аспекты использования продукта Рутокен Web для аутентификации в сети Интернет.
Cмотреть видео
Cмотреть видео