Поиск по тегу «technology» в разделе Видеокаталог
00:18:31
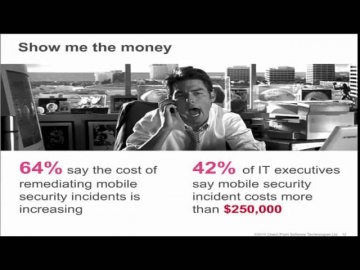
Check Point: The Security Zone Ep. 5: Impact of Mobile Devices on Information Security
teamed up with Dimensional Analysis to survey over 700 IT and security professionals in 6 countries to learn the current attitudes and trends regarding the impact of mobile devices on information security.
Cмотреть видео
Cмотреть видео
HD 00:05:44
Softline - Global IT Solution and Service Provider. India.
Softline - Global IT Solution and Service Provider. India.
Cмотреть видео
Cмотреть видео
HD 00:03:07
Check Point: Customer Success: AlmavivA Group
Almaviva, Italy's number one Information & Communication Technology provider, describes how Technologies protects the organizations infrastructure.
Cмотреть видео
Cмотреть видео
00:29:34
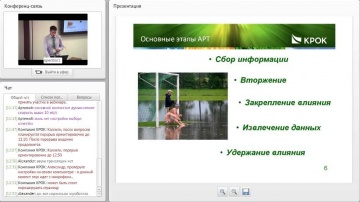
КРОК: Защита от направленных атак (APT)
05 июня 2014 Семинар "Next Generation Security: новый взгляд на интеренет-угрозы". Часть 4. Доклад "Защита от направленных атак (APT)" Луцик Павел, технический менеджер, КРОК
Cмотреть видео
Cмотреть видео
HD 00:01:44
Check Point: Customer & Partner Insights- California DMV
partners with hundreds of companies across the U.S. and internationally to form long-term business and person relationships. To learn more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as they share w...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
00:43:43
Check Point: Q&A: Compliance and Regulations with Jeremy Kaye | Network Security Risk and Compliance
For more information: On June 18, 2013, 's in house #regulations and #compliance expert Jeremy Kaye spoke with Dameon Welch-Abernathy live in our first Google+ Hangouts on Air. This was an opportunity to hear some of the challenges your p...
Cмотреть видео
Cмотреть видео
HD 00:03:04
Check Point: Choosing the Right Next Generation Firewall | NGFW Explained
For more information: What is a Next Generation Firewall, where did the term come from and why is leading this market.
Cмотреть видео
Cмотреть видео
HD 00:05:30
Check Point: Denial of Service Cyber Attack Protector Overview
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Modern DDoS attacks use new techniques to exploit areas where traditional secu...
Cмотреть видео
Cмотреть видео
HD 00:07:07
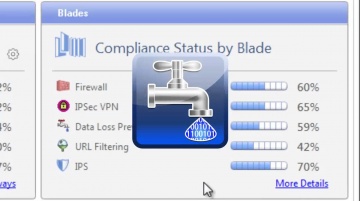
Check Point: Compliance Software Blade Demonstration
Introduction and overview to the Compliance Software Blade and its features and functions.For more information: The Compliance Software Blade monitors your management, Software Blades and security gateways to constantly validate that you...
Cмотреть видео
Cмотреть видео
HD 00:02:08
Check Point: 2013 Security Report | Cyber Security
Based on research of nearly 900 companies and 120,000 hours of monitored traffic, the 2013 Security Report reveals major security risks organizations are exposed to on a daily basis. For information: Most importantly, the report provides...
Cмотреть видео
Cмотреть видео
HD 00:02:14
GroupIB: Group-IB Bot-Trek | Botnet Monitoring and Cyber Intelligence
Group-IB Bot-Trek™ is a real-time botnet and cyber intelligence service that provides a direct access to compromised data and helps to prevent fraud. Bot-Trek™ gathers compromised data and intelligence from botnets and computer underground...
Cмотреть видео
Cмотреть видео
00:05:02
Check Point: on National Czech Republic Television
Eurograbber was launched against banking customers, using a sophisticated combination of malware directed at computers and mobile devices. For more information click here: The malware, in conjunction with the attackers' command and contr...
Cмотреть видео
Cмотреть видео
HD 00:14:29
Check Point: Radio Interview Discussing 2013 Cyber Security Threats
Kellman Meghu, Head of Security Engineering at speaks to The Biggs Radio Show about what cyber security threats we should look out for in 2013
Cмотреть видео
Cмотреть видео
HD 00:04:05
Check Point: Denial of Service Attacks & How to Protect Against Them
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Alon Kantor, Corporate Development Architect at talks about the threat of dist...
Cмотреть видео
Cмотреть видео
HD 00:00:50
1С:Первый БИТ: BIT Mobile автоматизация мобильных сотрудников
Получите бесплатный тест-драйв мобильного приложения для выездных сотрудников, оставив заявку на сайте http://superagent.ru/?utm_source=Video&utm_medium=Youtube&utm_campaign=VideoSuperagent
Cмотреть видео
Cмотреть видео
HD 00:07:06
Check Point: 's SSL Inspection Technology | Enterprise Network Security
This video shares 's SSL Inspection technology against internal and external threats: This video provides a close look at 's SSL Inspection technology, which allows 's advanced security functions -- including Application Control, URL Fil...
Cмотреть видео
Cмотреть видео
HD 00:02:39
Check Point: Makes DLP Work | Data Loss Prevention
's new DLP Software Blade combines innovative technology with a unique approach that blocks intentional and unintentional data breaches and educates employees in the process to help prevent future incidents. Watch this video to see how...
Cмотреть видео
Cмотреть видео
00:01:45
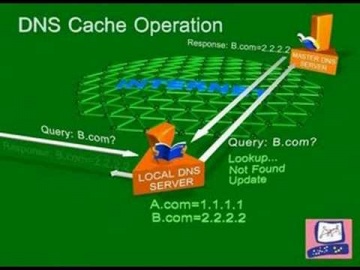
Check Point: DNS Cache Poisoning Attack | Internet Security
Software explains common DNS attacks. Learn More: DNS is the glue that holds the Internet, including web and e-mail together. A successful attack may severely impact the availability of an organization’s public facing web sites and e-mail...
Cмотреть видео
Cмотреть видео