Поиск по тегу «malware» в разделе Видеокаталог
HD 00:02:14
GroupIB: Group-IB Bot-Trek | Botnet Monitoring and Cyber Intelligence
Group-IB Bot-Trek™ is a real-time botnet and cyber intelligence service that provides a direct access to compromised data and helps to prevent fraud. Bot-Trek™ gathers compromised data and intelligence from botnets and computer underground...
Cмотреть видео
Cмотреть видео
00:05:02
Check Point: on National Czech Republic Television
Eurograbber was launched against banking customers, using a sophisticated combination of malware directed at computers and mobile devices. For more information click here: The malware, in conjunction with the attackers' command and contr...
Cмотреть видео
Cмотреть видео
HD 00:04:43
Check Point: Next-Generation Secure Web Gateway | Network Security
Learn More: Are you trying to secure Web 2.0 with 1.0 tools? The Web has evolved, threats have evolved, so should your Web Security! In this video, learn how to best protect against today's web-borne malware and help businesses to get th...
Cмотреть видео
Cмотреть видео
HD 00:14:29
Check Point: Radio Interview Discussing 2013 Cyber Security Threats
Kellman Meghu, Head of Security Engineering at speaks to The Biggs Radio Show about what cyber security threats we should look out for in 2013
Cмотреть видео
Cмотреть видео
HD 00:04:05
Check Point: Denial of Service Attacks & How to Protect Against Them
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Alon Kantor, Corporate Development Architect at talks about the threat of dist...
Cмотреть видео
Cмотреть видео
HD 00:13:44
Компьютерная вирусология: введение
Какое влияние вредоносные программы оказывают на рядовых пользователей, какую роль играют в развитии киберпреступности, как они распространяются и, наконец, как с помощью решений безопасности «Лаборатории Касперского» защитить свой бизнес -...
Cмотреть видео
Cмотреть видео
HD 00:02:00
Check Point: Anti-Bot Protection | IoT| Network Security
A bot is malicious software that allows cyber criminals to remotely control computers and execute illegal activities such as stealing data, spreading spam and distributing malware. More information: Anti-Bot security software detects bot...
Cмотреть видео
Cмотреть видео
HD 00:03:31
Check Point: Protecting Against Spy Eye Bot | Network Security
For more information: Learn how to protect against Spy Eye bot
Cмотреть видео
Cмотреть видео
00:01:45
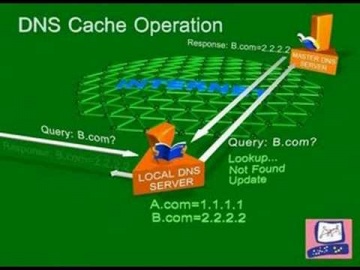
Check Point: DNS Cache Poisoning Attack | Internet Security
Software explains common DNS attacks. Learn More: DNS is the glue that holds the Internet, including web and e-mail together. A successful attack may severely impact the availability of an organization’s public facing web sites and e-mail...
Cмотреть видео
Cмотреть видео