Check Point: R80 Security Management плейлист

360 роликов
Нет подписчиков
Компания Check Point Software Technologies Ltd. — мировой поставщик решений в области обеспечения интернет-безопасности, единственный поставщик средств обеспечения полной безопасности Total Security для сетей, данных и конечных узлов, объединенных единой средой управления.
Check Point: R80 Security Management
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вредоносного ПО и отражения других типов атак.
предлагает законченную архитектуру безопасности, которая защищает и сети крупных организаций, и мобильные устройства, а также отличается наиболее полным и интуитивно понятным управлением системой безопасности. стал первопроходцем в индустрии с межсетевым экраном FireWall-1 и запатентованной технологией Stateful Inspection.
Check Point: Lightboard Series: Dynamic Revisions
This video elaborates on the logic behind the R80.10 Security Management architecture focusing on the dynamic revisions feature. This feature automatically stores the full history of database changes, with very little footprint, consuming ...
Cмотреть видео
Cмотреть видео
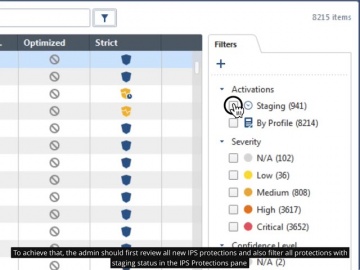
Check Point: R80.10 Policy Management – IPS Protections in Detect (Staging) State
This video elaborates on the logic behind new IPS protections status after IPS update operation and introduces best practice on changing the status of detect-staging on prevent when enough information was gathered regarding the new IPS prot...
Cмотреть видео
Cмотреть видео
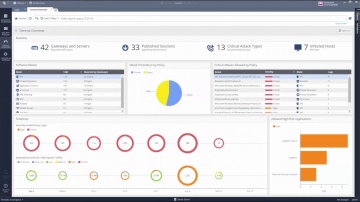
Check Point: R80.10 Logs and Monitor Pane – Key Components and Operations video
In this movie, we elaborate on the key components and operations of events management and reporting, within ’s R80.10 suite.
Cмотреть видео
Cмотреть видео
Check Point: Upgrading from R77.3O to R80.10 Via CPUSE
This video demonstrates in-place upgrade of a real customer database from R77.30 to R80.10 via CPUSE interface in the Web UI.
Cмотреть видео
Cмотреть видео
Check Point: Step-By-Step Guide for Securing a Web Server on Azure using CloudGuard IaaS (prev. vSE
Learn to create and deploy a web server on top of Azure public cloud and to securely publish it through a vSEC standalone server. More information:
Cмотреть видео
Cмотреть видео
Check Point: R80.10 Policy Revision
R80.10 Policy revision explained. Learn how to work with policy revision in R80.10. For more information: R80.10 features the most advanced threat prevention across networks and cloud, managed by a single security management console. Secu...
Cмотреть видео
Cмотреть видео
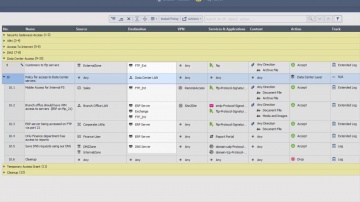
Check Point: R80.10 SmartConsole Security Policies View | Threat Prevention
This video is an overview that describes important features and functionality of the R80.10 SmartConsole and focuses on: Unified Access and Threat Prevention Policies Example of inline layers for zone-based policy Using multiple blades in o...
Cмотреть видео
Cмотреть видео
Check Point: Start Building Your Unified Policy with R80.10 | Security Management | Tech Bytes
R80.10 policy management is unified so you can create and monitor these policies harmoniously. One single policy manages your users, devices, applications, data and networks. With this unified policy, you also get unparalleled granular cont...
Cмотреть видео
Cмотреть видео
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architec...
Cмотреть видео
Cмотреть видео
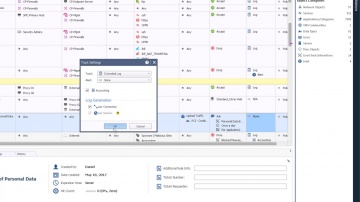
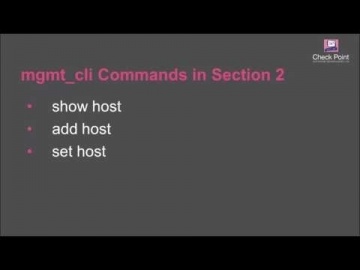
Check Point: Creating Host Objects with R80 Management API Tutorial | Security Management Tutorial
How to use R80 Management API to run a BASH script that automatically creates host objects in the Security Management server database. For more information: This video tutorial is intended for users that are familiar with automation scri...
Cмотреть видео
Cмотреть видео
Check Point: R80 Enhances Efficiency at the University of Kansas
The University of Kansas tested R80 security management and liked what they saw. Today they enjoy increased operational efficiency through concurrent administration capabilities, APIs for automation and a single pane of glass.
Cмотреть видео
Cмотреть видео
Check Point: R80 Streamlines Security Management at Appvion | Data Center Security
Appvion, a manufacturer of specialty papers, tested R80 security management during development and now uses it every day to gain efficiency, high visibility and concurrent management capabilities.
Cмотреть видео
Cмотреть видео
Check Point: Tutorial: Configuring Application Control
How to use R80 SmartConsole to get started with the Application Control, URL Filtering Software Blades, and URL Filtering Settings with R80 Security Management. For more information: Infinity, the first consolidated security across net...
Cмотреть видео
Cмотреть видео
Check Point: Tutorial: Configuring IPS Settings with R80 Security Management Server | Advanced Threa
How to use R80 SmartConsole to configure the settings for the IPS Software Blade. For more information visit:
Cмотреть видео
Cмотреть видео
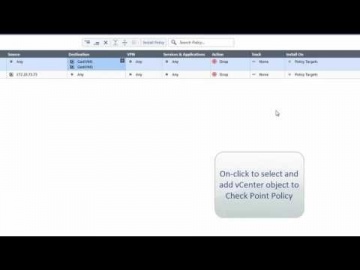
Check Point: vSEC controller Demo with R80 Smart Management | Cloud Security
This video demos the vSEC cloud security integration with VMware vCenter and NSX. It shows you how to integrate a vCenter server in the Smart Console, provision a security rule based on imported vCenter objects like VM name, integrate wit...
Cмотреть видео
Cмотреть видео
Check Point: Automation with VMware vCenter Orchestrator and R80 Smart Management
Use VMware vCenter Orchestrator to provision security policies in Ûªs R80 Smart Management Console leveraging the open API interface. This video demos automated security policy provisioning. Rules that are provisioned include Stealth rul...
Cмотреть видео
Cмотреть видео
Check Point: R80 Security Management | Advanced Threat Prevention
's R80 Security Management helps you consolidate security functions so you can be more efficient and effective at deploying the strongest protections across your organization. More Information:
Cмотреть видео
Cмотреть видео
Check Point: RSA 2016: R80 Security Management Launch | Security Management Software
For more information: Organizations that possess consolidated security simplify complex environments, improve efficiency and ensure security is consistently deployed across the organization. Change the way you manage security with integra...
Cмотреть видео
Cмотреть видео
Check Point: Security Management Customer Success Story: Talisys | R80 Security Management
More information on R80 Security Management visit Talisys, an innovator in financial securities processing software, leverages R80 to reduce security management complexity. Building on Ûªs leadership in speedy root cause analysis, they a...
Cмотреть видео
Cмотреть видео
Check Point: 24/7 Protection with ThreatCloud Managed Security Service | Threat Prevention
For more information visit ThreatCloud Managed Security Service is a cloud-based service providing actionable attack alerts for IPS, Anti-Bot and Antivirus customers. experts remotely monitor, manage and escalate attack incidents. Custo...
Cмотреть видео
Cмотреть видео
Показать больше