Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
Check Point: ThreatCloud | Complete Cyber Security Intelligence Infrastructure | Network Security
For more information: Introducing ThreatCloud, the first collaborative network to fight cyber-attacks.
Cмотреть видео
Cмотреть видео
Check Point: Overview of the 61000 Appliance | Data Center Security Systems
For more information:
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Partner Insights - Dataway
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Heather Zalatimo from partner Dataway shares thoughts about 's superior management capabilities and what makes her a fan.
Cмотреть видео
Cмотреть видео
Check Point: Threat Intelligence | Threat Prevention
Learn More: In 2012, established ThreatCloud, the first collaborative security infrastructure to fight cybercrime. ThreatCloud dynamically reinforces Threat Prevention Software Blades with real-time threat intelligence derived from res...
Cмотреть видео
Cмотреть видео
Check Point: 04 Installing the OVF Package and Configuring Global Parameters
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
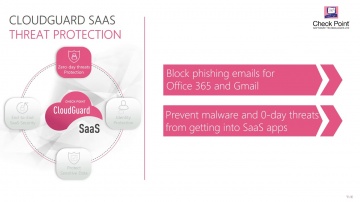
Check Point: CloudGuard SaaS Demo Series: Protecting Sensitive Data
For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and sensitive data protection for SaaS applications such ...
Cмотреть видео
Cмотреть видео
Check Point: Capsule Docs - Secure Business Documents Everywhere | Network Security
Capsule Docs ensures that only authorized individuals can access your business documents. Confidently share documents with coworkers, business partners, clients, and vendors, because you are in control of their access and sharing rights.
Cмотреть видео
Cмотреть видео
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Customer Insights - Leidos
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Joseph Royal of Leidos shares what makes him a fan.
Cмотреть видео
Cмотреть видео
Check Point: 03 Adding the vCenter IP Address to the Runtime Settings
VMware requires you to add the vCenter IP address to the Runtime Settings tab on the vCenter Server Setting page
Cмотреть видео
Cмотреть видео
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
Check Point: Zero-day Threat Protection for SaaS Email | CloudGuard SaaS Demo
Demo showing how CloudGuard Saas provides advanced security and threat prevention for SaaS applications. For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (Saa...
Cмотреть видео
Cмотреть видео
Check Point: Malware Threat Prevention | Zero-Day, Zero-Second.
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As ...
Cмотреть видео
Cмотреть видео
Check Point: Capsule Docs – Keep Your Business Documents Protected | Enterprise | Network Security
Capsule Docs protects your sensitive business documents to ensure they don’t get unintentionally exposed. See how Capsule Docs works to provide document security.
Cмотреть видео
Cмотреть видео
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Customer Insights - Securities America, Inc.
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Leon Johnson from Securities America, Inc. speaks about the critical need to secure data in the financial industry and how integrates ...
Cмотреть видео
Cмотреть видео
Check Point: 02 Configuring Agent VM
To use a local Datastore on multiple ESX hosts (recommended) for the vSEC Gateway, or to use a non-distributed vSwitch for vSEC Gateway communication to the Security Management Server, you must configure Agent VM settings
Cмотреть видео
Cмотреть видео
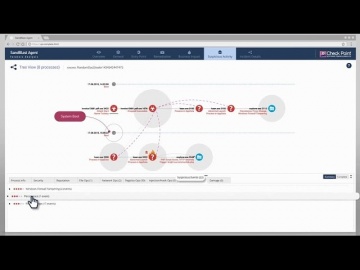
Check Point: SandBlast Agent Forensics
This video shows SandBlast Agent’s automated forensics analysis in action. For more information: It demonstrates SandBlast Agent’s power to instantly provide security teams with a crystal-clear understanding of cyber attacks, empowering t...
Cмотреть видео
Cмотреть видео
Check Point: Gen V Cyber Security with Moti Sagey - CPX 360
In his keynote, Moti Sagey will discuss in a pragmatic fact based way what it takes to build a Gen V security solution and how the cyber landscape matches the must have for effective security.
Cмотреть видео
Cмотреть видео
Check Point: Stop Advanced Mobile Threats Before They Start | SandBlast Mobile Security
Learn More: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: Cyber criminals may be stealing data from your smartphone or tablet without your knowledge. They’re experts at exploiting vulner...
Cмотреть видео
Cмотреть видео
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
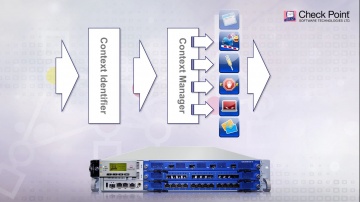
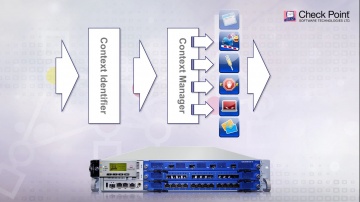
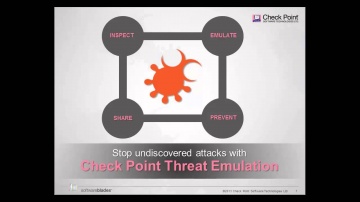
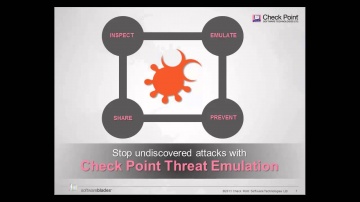
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
Check Point: Customer & Partner Insights- FishNet Security
Learn More: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as they share what makes them a fan.
Cмотреть видео
Cмотреть видео
Check Point: 01 Installing the Management Server Hotfix
Install the Hotfix on Gaia R77.30 Security Management Server and R77.20/R77.30 Security Gateways. It is required for both the vSEC Gateway and the vSEC Controller.
Cмотреть видео
Cмотреть видео
Check Point: Introducción a Compliance Blade
Introducción a Compliance Blade a Software
Cмотреть видео
Cмотреть видео
Check Point: Protecting Against Spy Eye Bot | Network Security
For more information: Learn how to protect against Spy Eye bot
Cмотреть видео
Cмотреть видео